July’s Crowdstrike outage, perhaps the largest IT outage in history, resulted in more than $5 billion in losses for Fortune 500 companies. But it also highlighted another issue – the U.S. government’s crippling dependence on Microsoft.
When CrowdStrike issued an update to its Falcon cybersecurity software, millions of computers using Falcon and Microsoft Windows crashed. Many government agencies essentially shut down while a fix was deployed. According to FedScoop, the outage affected at least a dozen federal departments and agencies, from FEMA to the State Department.
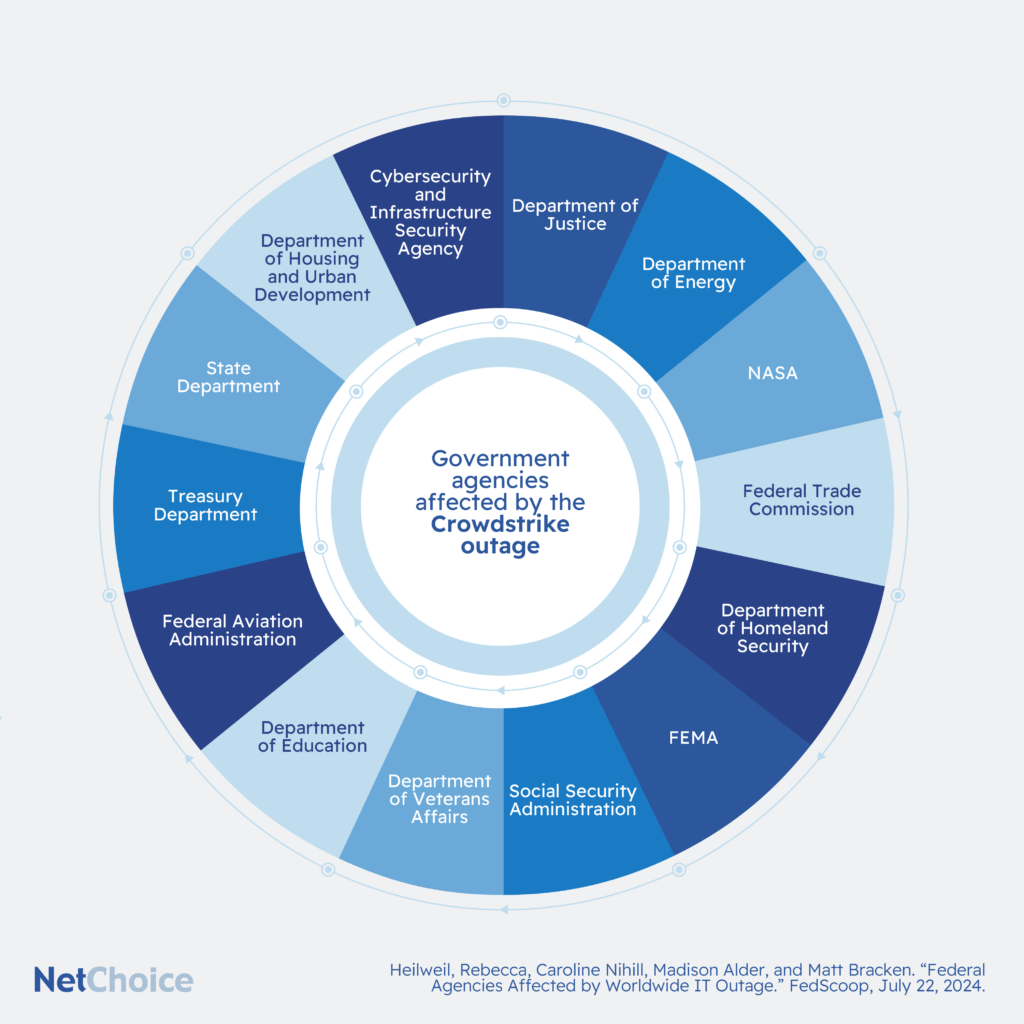
Crowdstrike and Microsoft are different companies, so Crowdstrike’s error wasn’t Microsoft’s. But the outage sparked renewed attention to the fact that Microsoft “controls an astonishing 85% share of federal productivity software,” and an even higher percentage of operating systems within the U.S. government. This represents a single point of failure that puts critical government information and services – including everything from 911 to the U.S. power grid and classified defense technology – at risk.
The government’s reliance on Microsoft makes it “a magnet for cybercriminals and government hackers,” explained WIRED’s Eric Geller in an April 2024 article. The magazine first called out the dangers of a “Microsoft monoculture” in 2004.
The risks of this monoculture are increasing. In the past three years, major Microsoft breaches have had disastrous results:
- 2020: Russian hackers accessed the systems of multiple government agencies, allowing the hackers uninterrupted access to confidential information (SolarWinds hack).
- July 2023: Chinese hackers gained access to the email systems of several U.S. government agencies and think tanks, affecting approximately 10,000 organizations.
- September 2023: Chinese hackers breached Microsoft’s email platform, stealing approximately 60,000 emails from 10 U.S. State Department accounts.
As the world’s largest customer, the U.S. government has a responsibility to diversify its IT ecosystem to protect the lives, information and privacy of the Americans it serves. A June survey sponsored by NetChoice and conducted by Morning Consult found that 73 percent of registered voters agree that the U.S. government should reconsider business with companies that are frequently hacked.
But Microsoft’s hold on federal agencies remains “almost untouchable.” Even in the face of regular breaches, “while some agencies are exploring alternatives to Microsoft, most of them are sticking with what they know.”
Part of the problem is what’s known as “vendor-lock,” in which a provider makes it extremely difficult for a customer to contractually switch to another vendor because of incurred costs, technical barriers or operational impact. So even though Microsoft charges government customers extra for security protections like threat monitoring and antivirus – which other providers include at no extra cost – agencies are hesitant to switch.
Ultimately, however, vendor-lock in U.S. government agencies is about short-term inconvenience and cost at the possible expense of long-term security. Addressing the issue of vendor-lock will require accountability of practices industry-wide, not just within the government.
Agencies can also look to explore alternative security products or add additional solutions, such as encryption software that provides another layer of defense if Microsoft’s systems are breached. The government can also increase pressure on Microsoft by allowing for more rigorous security audits of its products.
Whether it’s an outage or a breach, it’s only a matter of time before the government’s systems are put at risk again. It’s time for oversight on these flawed systems.
